The world is a mix of good and evil. What’s disheartening is, the combination is not balanced at all. You might find some people who are too good to be true, and some you don’t want to meet ever again.
This is a regular instance in ordinary life.
And the digital world is no different. It would be stupid to consider that there are only good things happening in the tech world; many entrepreneurs have and continue to become prey to malicious hackers’ fraudulent acts.
These activities can dramatically impact the current market standing, brand reputation, and financial holding of a business owner.
But to every villain, there is a superhero, right? These frauds can not let your business down if you have machine learning to support you.
As the BBC fraud expert, Aslam Muhammed says,- ML can effectively protect your hard-earned assets. We believe so as well.
To understand this more deeply, we’ll have to elaborate on what exactly is Machine Learning and how it can affect your mobile application development and save it from any fraud it may encounter in the present or future.
Machine learning is considered one of the trustworthy technology trends that can help fight global digital fraud- identifying the threats of the increasing complexity of the entire payment ecosystem.
The primary attraction for fraudsters is the path with the least resistance, which signifies why it is imperative to integrate machine learning into your technology project.
Machine learning smartly uses artificial intelligence for running software applications by predicting outcomes without the need for programming.
Machine learning offers various versatile features such as image recognition, email spam detection, and product recommendations for businesses owning an e-commerce platform or some other Business Process Automation (BPA).
Having said that, let’s further understand the intricacies of machine learning because it can only be properly implemented once you know the a to z of it.
What are the Various Types of Machine Learning?
The true definition of machine learning would be-the act of an algorithm working to achieve the power of accurately predicting the future. It can be divided into four categories, namely:
- Supervised Learning
- Semi-supervised Learning
- Unsupervised Learning
- Reinforcement Learning
Let’s dive deeper into knowledge:
The types of algorithms:
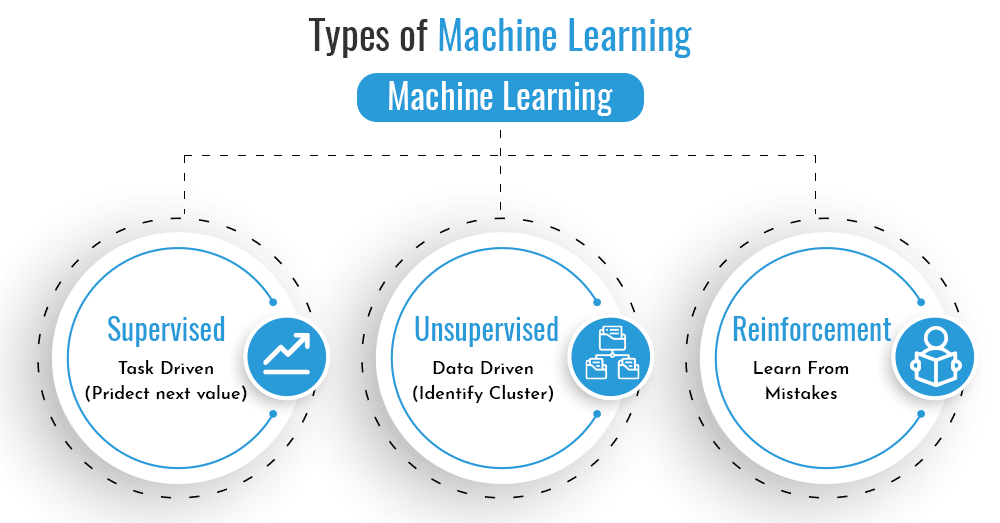
- Supervised Learning:
This type of machine learning is entirely supervised; we are talking about the procedure. The process consists of supplying algorithms attached to labeled training that can assess the correlations.
Data scientists can supply these algorithms in this type of machine learning for defining the variables.
- Semi-supervised Learning:
This approach involves mixing the two preceding types. Data scientists can feed an algorithm with labeled training data in most cases, but the model will remain free to individually access and explore the data. This will also help in developing its knowledgebase of the data set.
- Unsupervised Learning:
The unsupervised machine learning involves algorithms that are trained on unlabeled data. Such algorithms scan the entire datasets to attain meaningful connections. Both the predictions or recommendation output and the data these algorithms train on are pre-merged.
- Reinforcement Learning:
This type of machine learning is considered valuable in completing the multi-step process of defining the rules clearly. Also called the “wait and watch technique” by many.
Many mobile apps development companies prefer to program an algorithm and expert data scientists to complete a task while imparting negative and positive cues.
Now that we understand machine learning dynamics, it is time to find out how ML can work as a protective layer against any fraudulent incidents.
Why is ML the Best Way to go to Avoid Digital Fraud?
- Lightning Fast:
The speed of your action plan is essential in pinning down all the fraudsters. If your approach is retarded or you are too laid back, it won’t take even a minute for a fraudster to get access to all your crucial data.
Think and recall how much time it takes when you switch on the bulb, and it lits up? I think some fraction of seconds. This is precisely the approach ML moves forward with. The incredible technology can run multiple real-time analysis along with thousands of queries, comparing the outcome with the best results simultaneously.
ML works with an ongoing process of queries to identify the best possible results. It allows the app owner to understand customer behavior, so when an oddity arises, it is possible to flag or block a payment review.
- Scalable:
Let’s be honest; if there’s any online business rocking the market, it’s e-commerce or other transaction-based companies. Thus, the transaction volume has seen a significant rise as technology advanced.
The increased amount of customer data at digital sources and online payments has put extra pressure on the rules library to expand.
However, Machine learning believes “the more, the merrier.” Therefore, it can manage heavy loads of data conveniently and efficiently.
Let’s understand this with a metaphor- a car would give better performance and mileage while driving a long distance.
Similarly, Machine learning works better with massive datasets since it is a mixed bag.
The model considers both good and bad consumers; therefore, it becomes easy for ML to predict future frauds and avoid them at all costs by understanding user behavior.
- Accurate:
Matching pace with subtle and non-intuitive trends is a challenging task for humans.
However, ML can function extraordinarily in these arenas, surpassing the capabilities of a human. Thus, many companies prefer using ML to predict fraud during their mobile application development.
Machine learning can effectively interpret normal behavior in a better way. Therefore, it can raise a flag whenever it senses any malicious activity. It can identify a network even when there is no chargeback. Also, it helps in identifying suspicious signals. Therefore, using it, you can get a fair idea of copying and pasting data.
Fraud Detection Algorithm with Unsupervised Learning:
If fraud is an abnormal activity or other irregular behavior, then there are no surprises. Unsupervised learning allows the ML developer to understand the hidden pattern in transactions and facilitate self-learning. Through self-learning, fraud patterns can be noticed and ignored.
How Does Unsupervised Machine Learning Work?
This kind of ML algorithm doesn’t rely on labeled data- they can move through the unlabeled data to identify the patterns used for grouping data points into subsets.
These algorithms are well-suited for the following tasks:
- Anomaly Detection: Finding out the unique data point in the data set.
- Clustering: Segregating the data into groups of reality
- Dimensionality Reduction: Datasets use reduced variables
- Association Mining: Identifying the sets of items in a dataset that occur randomly in a bundle.
Possible Channels of Faulty/Fraud data:
The following are the possible channels through this fraud activity can barge their way into your data:
- Increase in traffic on new transactions, e.g., a customer has added 15 new payment cards within an hour.
- Phishing, mismatch or customer id with card details, and other irrelevant data.
- It can be a consumer ordering many expensive or luxury items.
- Orders received from an unknown location or shipping address is a fraud hotspot.
These are some examples that are considered shady and are mostly flagged as high-risks.
When the machine makes a prediction, the following are the steps to be taken:
- Input data
- Extract features
- Train algorithms
- Build a model
- Input Data:
This technique is considered one of the best when the data is vast in numbers.
While working with unsupervised learning, it is vital to segregate data into two segments: right and wrong.
- Extract Features:
This step consists of describing customer patterns and behaviors while flags are raised for fraudulent activities.
These features are categorized into five segments:
- Identity:
Consists of crucial details such as the number of digits in the customer email address, the number of devices used by the consumer, validity of account, and fraud rate of the customer’s IP address.
- Payment Method:
Consists of the issuing bank’s fraud rates, the similarities between customer name, and holding of cards from other countries.
- Network:
Consists of phone numbers, emails, or payment methods are shared within a customer’s network or any other network.
- Locations:
Must check if the shipping address matches the billing address. The shipping country should match with the customer’s IP; this decreases the threat of fraud at the customer location.
- Train Algorithm:
Solving any complex problem would need the help of an algorithm- a set of rules. For example, if you are solving a mathematical equation or programming task. It will use customer data to make predictions, e.g., genuine or fraud.
At the start, this data is used on algorithms: an online seller historical data is known as a training set.
The more fraud this training set has, the better it will be for the machine since it will learn from many examples.
- Build a model:
Once you have completed the training, you can move forward to creating a business-specific model that will help you detect fraud in a fraction of seconds. However, you must keep a keen eye on the model to ensure its proper functioning and stable improvement.
You can utilize this to improve, upload, and update a new model specific to each client; it will also pay attention to emerging techniques to make the process better.
Once you are done with training, it is wise to check the model’s working and ensure it is properly functioning. The model can effectively and accurately diagnose frauds and deploy them to analyze the business transactions made online.
Conclusion:
Machine learning provides a mobile apps development company to build the application to drudge all fraudulent activities while making online transactions. With a particular mechanism working to establish excellent security, the company can reinforce the payment gateway by conveniently adding more security layers.




